Publications
A study for the implementation of ROSI (Return on Security Investment)
Amir Ameri 2013 / UBS
Authors: Amir M. Ameri
This documentation presents an overview for the implementation of ROSI "Return on Security Investment", as presented in a CISO seminar in Berlin.
IT Compliance
Amir Ameri 2013 / UBS
Authors: Amir M. Ameri
This documentation provides an overview of the financial crises (2008-2012) and the impact on IT Compliance, and proposes a framework for IT Compliance. This publication was first prepared for presentation at a Compliance Seminar in Germany (2013).
Managing Information Security
Amir Ameri 2012 / UBS
Authors: Amir M. Ameri
This documentation provides an overview of how Information Security may be implemented and managed within a global organization, as presented in the CISO Seminar Zurich 2012.
Information Security Risk Management
Amir Ameri / Zurich Insurance Risk Engineering Unit 2005 – 2008 – 2010
Authors: Amir M. Ameri
This publication contains an overall history and overview documentation in the form of a slide set, covering the development of Information Security and Risk Management for Information Technology.
3-Dimensional Risk Analysis
Amir Ameri 2005
Authors: Amir M. Ameri
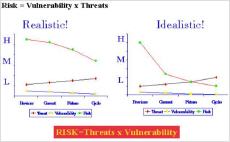
In this article, an alternative methodology for Risk Assessment is proposed. Where as a standard risk assessment takes into account impact and probability (or rate of occurrence), in this publication I investigate the possibility for a risk assessment conducted against the variables (Risk, Governing Boundary and the time span of today to a given time frame in the future eg. 3 or 4 or 5 years).
If you are interested in a copy of the full article, please send me an email.
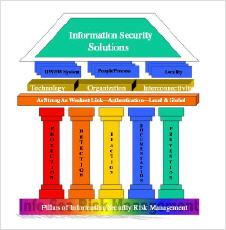
The Five Pillars of Information Security
Risk Management Magazine 2004
Authors: Amir M. Ameri
This article describes 5 fundamental principles for a Risk Management framework in the implementation of an Information Security posture in any size company.
"Ameri, A. (2004). The Five Pillars of Information Security. Risk Management, 51(7), 48"
Note: If you are interested in the full none edited version of this article, drop me an email.
Risk Management in Information Technology: A Model for Qualitative Risk Analysis
Southern California University 2003
Authors: Amir M. Ameri
In my dissertation, I worked on the development of a risk assessment model called "e-RAIS". This model, relies on a holistic and multi-faceted risk assessment for any size IT environment, considering the application & infrastructure landscapes, including processes and locality. Main contribution of the e-RAIS model is in the identification step, where the probability of identifying a "day-0" vulnerability is increased.
Part of my dissertation is available as public information. If you have interest in obtaining an electronic or hard copy, drop me an email.
Scanners de vulnérabilité: controler le réseau
DECISION : MICRO & RESEAUX December 9, 2001
Authors: Amir M. Ameri, Jerome Saiz
This article as published in the Decision magazine, was written by Jerome Saiz, to which I contributed the information relevant to the definition and implementation of a penetration testing environment for my employer at the time Zurich Insurance.
For a copy of this article (in French) please send me an email.
Case Study by Shreese Richardson
Shreese Richardson 2014
Authors: Shreese Richardson
This Case Study was solely made by Shreese Richardson on the the following publication:
"Ameri, A. (2004). The Five Pillars of Information Security. Risk Management, 51(7), 48"
Analysis of Ameri's Five Pillars of Information Security
Brian Zaugg 2010
Authors: Brian Zaugg
This Analysis was solely made by Brian Zaugg on the the following publication:
"Ameri, A. (2004). The Five Pillars of Information Security. Risk Management, 51(7), 48"
A Critique of Amir Ameri's "The Five Pillars of Information Security"
Brian Opalewski
Authors: Brian Opalewski
This Critique was solely made by Brian Zaugg on the the following publication:
"Ameri, Amir. (n.d). The Five Pillars of Information Security. Retrieved July 18, 2014, from
http://cf.rims.org/Magazine/PrintTemplate.cfm?AID=2409"
Brian Opalewski writes: "If the author intends to describe the fact that there can never be any control over the threat environment, only of the vulnerabilities or attack surfaces, ..."
Note: Brian's point is absolutely correct. If you are interested in the full version of the article, drop me an email.